Features:
* Rendering Engine - K-Ninja utilises the latest SeaMonkey/Gecko Rendering Engine release. It is a fast, secure rendering engine which supports most current Web Standards (HTML 4.0, CSS, XHTML etc.).
* Tabs - K-Ninja has tabbed browsing, which we call "Layers". New layers can be opened and closed with the Open & Close Layers buttons.
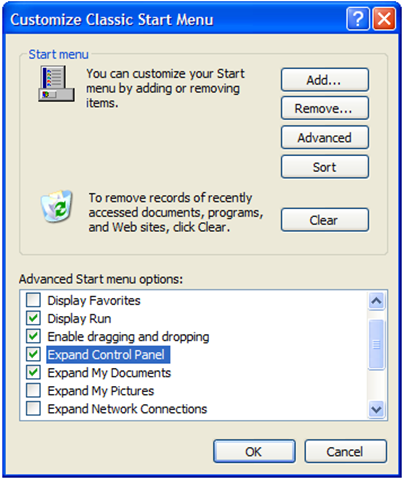
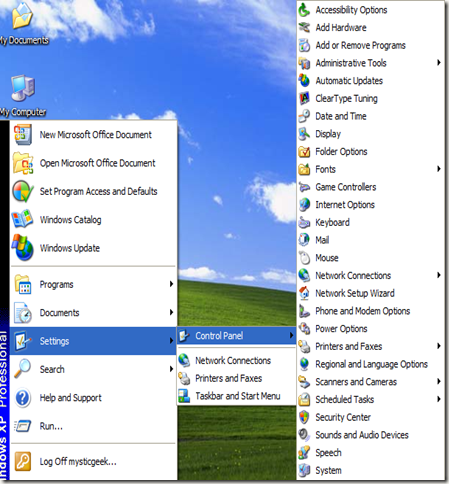
* Compact Menu - to increase viewing space, the menu which is normally located at the top of the screen is available in K-Ninja via the Preferences button, by right-clicking on it.
* Pop-up Blocker - Enabled by default, K-Ninja will block most if not all pop-ups. The pop-up blocker can be enabled/disabled via the Preferences button.
* RSS Support - the Aggreg8 RSS Reader is included with K-Ninja. It can be accessed via the Compact Menu (right-click on the Preferences button). Tools -> Mail and News.
* Mouse Gestures - the mouse gestures plugin is included. To use simply right-click, hold the mouse button and then drag the cursor either right (to go back a page) or left (to go forward).
* Translate a Page - simply right-clicking on a webpage will provide you with a menu to translate a page from one language to another.
* Mozilla ActiveX Control support included for Media Player functionality on streaming and embedded multimedia content. To enable support, go to Tools -> Applications -> ActiveX *Media Player* Control. You will then need to restart K-Ninja for it to work.
* Flashblock extension - this can be enabled/disabled via the Compact Menu. To access, goto: Tools -> Privacy -> Permissions -> Flashblock. Once enabled Flash animations will be deactivated on the webpages you are viewing.
* Extremely lightweight STP MP3 Player included (200kb). STP can be accessed via the Compact Menu: Tools -> Applications -> STP MP3 Player, or pressing ALT + N will run STP as well. When run an icon for STP will appear in your System Tray. Right click on the icon for options or to play an MP3 or CD whilst browsing.
* Now includes additional Web Search engines including MultiSearch: enter a search term and the results will be delivered via 6 popular search engines including Google (100 results per page), MSN, All The Web, Google Images, Ask.com & Gigablast.
* Built in macro language.
* Unique themes & skins.
* Even more privacy options available via the Compact Menu. Tools -> Privacy will provide you with an array of options to enable/disable any "features" that you don´t want running on a webpage before you view it (like Java, Javascript etc).
Download
Portable :Read More..
http://filestorage.gatzet.com/download.php?file=e8681615e9b6fba791eb9261eb498a26
http://k-ninja-samurai.en.softonic.com/
size : 7 MB











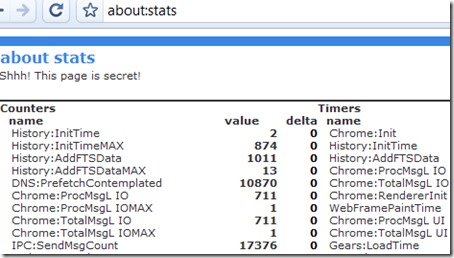
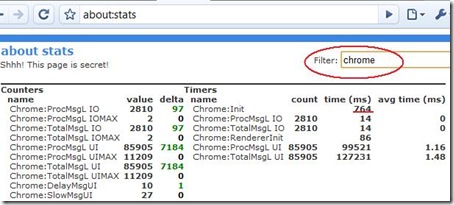
 Ahead of the hotly anticipated T-Mobile G1 smartphone's arrival in stores next week, early reviews show not everyone is convinced that the Android-powered handset is ready to take on the Apple iPhone or muscle onto the turf of Windows Mobile or the BlackBerry.
Ahead of the hotly anticipated T-Mobile G1 smartphone's arrival in stores next week, early reviews show not everyone is convinced that the Android-powered handset is ready to take on the Apple iPhone or muscle onto the turf of Windows Mobile or the BlackBerry. 






 You might not be aware of this, but even if you tell Windows to show all file extensions there are still some that are hidden by default. Also, any installed program can configure extensions to be hidden. This is why you will find a special window in Hacker Eliminator that will show you what extensions are being hidden and allow you to toggle them unhidden. Extensions window in the Hacker Eliminator menu will automatically mark any potentially dangerous hidden extensions in red, so that you will know which ones to toggle to unhidden. Here are a couple of examples on how this works and why some hidden extensions could be a danger to some computer users. Assuming that you already configured Windows explorer to show all extensions:
You might not be aware of this, but even if you tell Windows to show all file extensions there are still some that are hidden by default. Also, any installed program can configure extensions to be hidden. This is why you will find a special window in Hacker Eliminator that will show you what extensions are being hidden and allow you to toggle them unhidden. Extensions window in the Hacker Eliminator menu will automatically mark any potentially dangerous hidden extensions in red, so that you will know which ones to toggle to unhidden. Here are a couple of examples on how this works and why some hidden extensions could be a danger to some computer users. Assuming that you already configured Windows explorer to show all extensions:  Because there are only a handful of these startup methods, we find more hackers going to extremes to find new methods of startup. This includes using dangerous changes to the system registry, which will rend the system useless if the trojan file or it's companion file is ever removed. This is one reason not to use standard anti virus software to remove trojans. If one of these methods are used, and the file is removed without fixing the system registry, your system may not be able to run any programs after you reboot. Hacker Eliminator detects and repairs all of these dangerous startup methods as seen with this Sub7 infection.
Because there are only a handful of these startup methods, we find more hackers going to extremes to find new methods of startup. This includes using dangerous changes to the system registry, which will rend the system useless if the trojan file or it's companion file is ever removed. This is one reason not to use standard anti virus software to remove trojans. If one of these methods are used, and the file is removed without fixing the system registry, your system may not be able to run any programs after you reboot. Hacker Eliminator detects and repairs all of these dangerous startup methods as seen with this Sub7 infection.